In the era when data is gold, it is being leveraged positively to resolve countless problems related to inefficiencies, unproductivity, issues during operations, and whatnot. For instance, AI is now being used across industries to power data-driven decision-making and yet, there are some ill-uses too. Cybercriminals or cyber attackers use the internet as a means to leverage small to large-scale attacks troubling businesses, and stealing critical business and customer data to name a few.
Why is Cybersecurity a Matter of concern?
Be it corporate scams, espionage, business disruption or even national-level threats, cyberattacks are becoming prevalent. Be it a bank or law firm or healthcare, educational institute or government organization. All these are prone to cyberattacks which is why ‘cybersecurity’ becomes a key aspect that companies spend millions on. It is estimated that almost $172 billion was spent on cybersecurity in 2022 and the numbers are only compounding.
Statistically speaking, the global cost of cybercrime according to the Official Cybercrime Report 2022 dictates the global cost of cybercrime in 2023 is estimated to rise from $8 trillion in 2023 to $10.5 trillion in 2025. A separate report points out how identity fraud affected 42 million people in the U.S. and incurred $52 billion in losses.
At the moment, the scourge attack on the supply chain is estimated to be one of the largest affecting 45% of global organizations that deal with the supply chain in one way or another. Cloudflare reported one of the largest ransom DDoS cyberattacks involving 2.5Tbps that happened in the third quarter of 2022. It even reported a 67% rise in the ransom DDos attacks YoY in 2022.
Current Cybersecurity Threats & Solutions
Time and again, there have been multiple cybersecurity threats that have exploited systems worldwide. Asking for ransom, control, autonomy, or capturing of sensitive data to use against individuals, companies, and even governments. With that being said, there are varied types of threats that are lurking in the hindsight awaiting exploitation if a backdoor is open.
Also Read: Bluebugging: What Is Bluetooth Hacking & How To Be Safe From It?
Malware

The most common security threat, malware is any malicious software that includes viruses, ransomware, spyware, etc. These can infect your system when you click on an email attachment or link. It can be from multiple sources but can be protected against with relative ease. You shouldn’t click on any email or link that appears suspicious or has a high spam count. Apart from that, updating the system from time to time fortifies its resistance against malware.
To prevent such types of attacks, you must keep the system updated. It is a common practice that we usually keep outdated or unused apps installed. But they can be used as a means of exploitation leading to backdoor access to the system.
Denial of Service Attack (DoS)
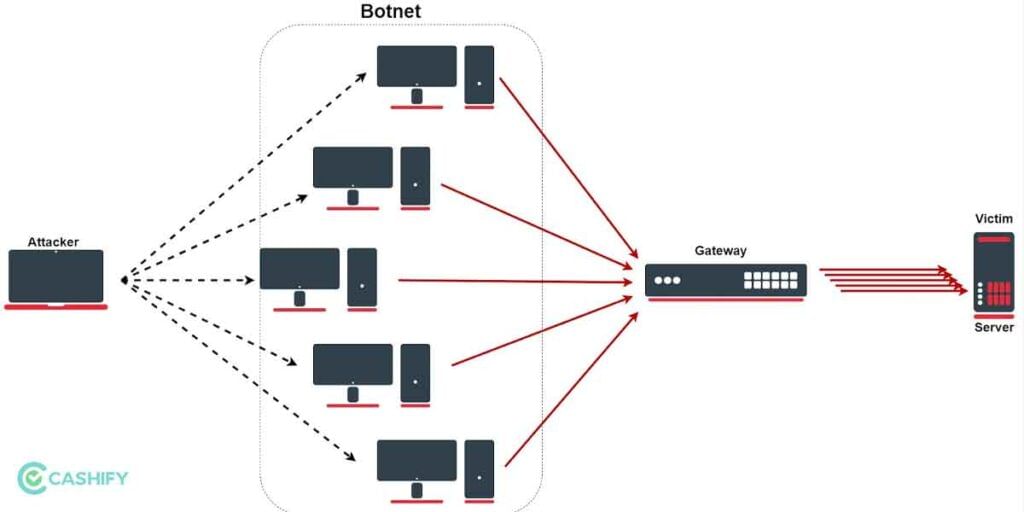
DoS is aimed at shutting down or disrupting a network with higher traffic flow making the intended users unable to access it. The attack uses traffic to float the target machine thereby crashing it as it doesn’t have any resources available to serve actual users. You might have heard about Distributed Denial of Services (DDoS) in movies which is committed by launching infected devices onto the target system.
Also Read: Cyber Swachhta Kendra: How To Keep Your Devices Bot Free?
Zero-Day Exploit

A zero-day exploit is an attack instigating a software/system that neither the software vendor nor the antivirus knows about. These are new threats that are still unknown and thus, there’s no definition to fix even if you have the latest antivirus program installed on your system. Web browsers are typically the common actors targeted by such attacks. Also, government organizations, systems with large numbers of devices especially IoT, and large enterprises are often the victim of these types of attacks.
There are a few methods to detect such attacks although we won’t recommend them to beginners. There’s CPU Level Inspection, and malware DNA analysis among others can be used to detect such exploits.
Social Engineering Attacks

In this type of attack, instead of using bots, attackers target a human’s emotions, behaviour, and interaction as the core to fool them into getting something done. Humans can make errors and that’s where social engineering attacks take flight. An attacker could fool an employee disguising himself as a colleague or someone with authority to share sensitive data or get access to some portals. It can also include breaking certain security protocols or instructions.
Companies are required to train their employees to recognize such attacks. This can help the respective IT department protect the system against potential damage that the social engineering attack can bestow upon the entire organization.
Also Read: How To Create A Strong Password And Beat Security Experts And Hackers
Phishing
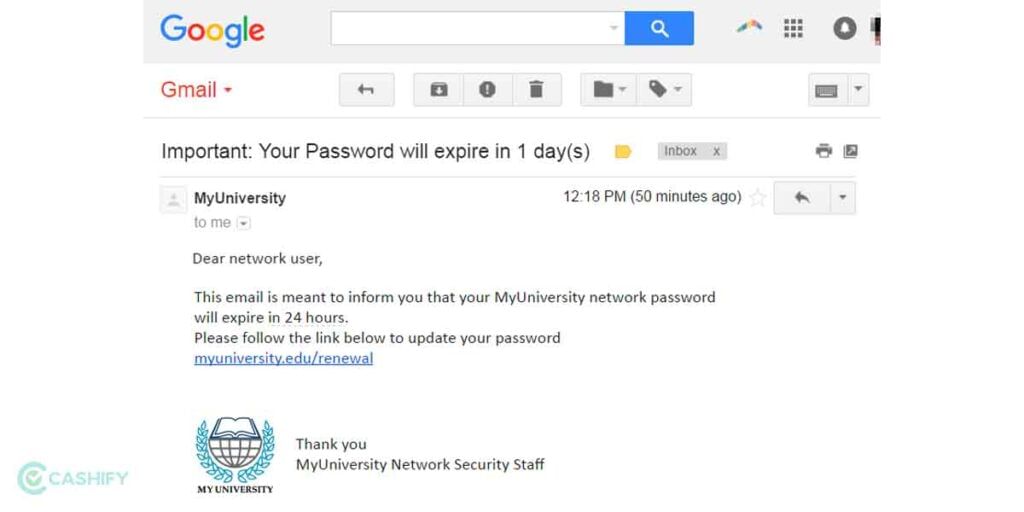
We already covered social engineering attacks and phishing is one of the many types of the same. It is common where hackers to disguise a website to look legit such as that of the target’s bank or social media profile. As the target enters credentials and provides sensitive information, it is automatically stored. Here, attackers have the opportunity to inject malware such as through malware or SMS.
There’s also an SMS-based phishing called Smishing which again uses humans to click on links sent via SMS. The users/employees should be trained in this account to recognize phishing attacks and steer clear of such incidences. Users should look for signs of a fake website such as spelling mistakes, slight variations in logo, and other areas that can signal if a website is legit or not.
Man-in-the-Middle Attack
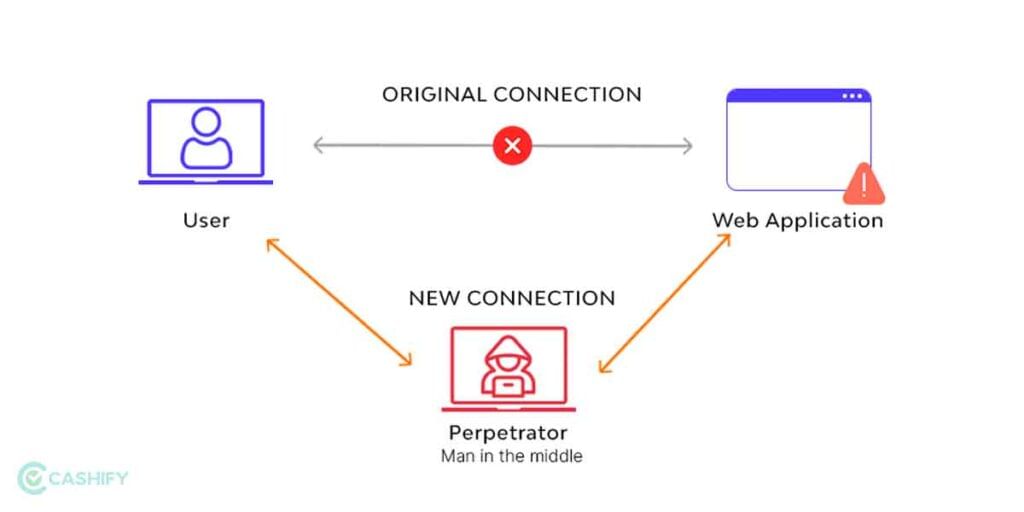
If you have ever played the game ‘Monkey in the middle’, you would understand this attack. Here, the cyber attacker gets access to the line of communication between points A and B. Here the hacker middleman takes advantage of the channel modifying or stealing it as it deems fit. It can be done through DNS, IP, HHPS, and even email and Wi-Fi.
Best Practices To Safeguard Against Cyberattacks
According to stats by the Theft Resource Center (2021), the number of cyberattacks rose from 928 in 2019 to 1,613 in 2021 and the number keeps on increasing. These numbers are shocking given our dependence on the web and how cybercriminals shifted their modus operandi from mass data misuse identity theft to identity fraud.
1. Opt for a people-centric approach
It might seem counterintuitive since mistakes from people are involved in cyberattacks at times. But you need to know that going for a people-centric instead of a technology-centric approach will pay off in the long run. A company operates with hundreds and even thousands of employees. And each having access to systems that can be used against an organization by hackers.
Thus, it becomes imperative to educate employees and workers about possible threats and how hackers can exploit any weak links. A proper corporate training session with information on the types of threats, solutions, and practices to prevent in the future will help safeguard sensitive data that can put employees, customers, and organizations at risk.
2. Educate Employees About Common Phishing Techniques

Click on a video on YouTube that might sound promising but isn’t, that’s what clickbait is. Turns out cyber attackers use similar techniques called phishing to lure users into entering the credentials. These can include login details for an important database or banking credentials that will leak out financial standings.
Phishing has some variants but pretty much everything works on the same sauce. There will be a convincing email, link, SMS, or others, that might seem legit until you provide the details asked such as login credentials, credit card details, and so on. The instances of phishing attacks have aggravated. Turns out, using spam filters, and always following protocols on what links to click and whatnot offers an overall defence against such attacks.
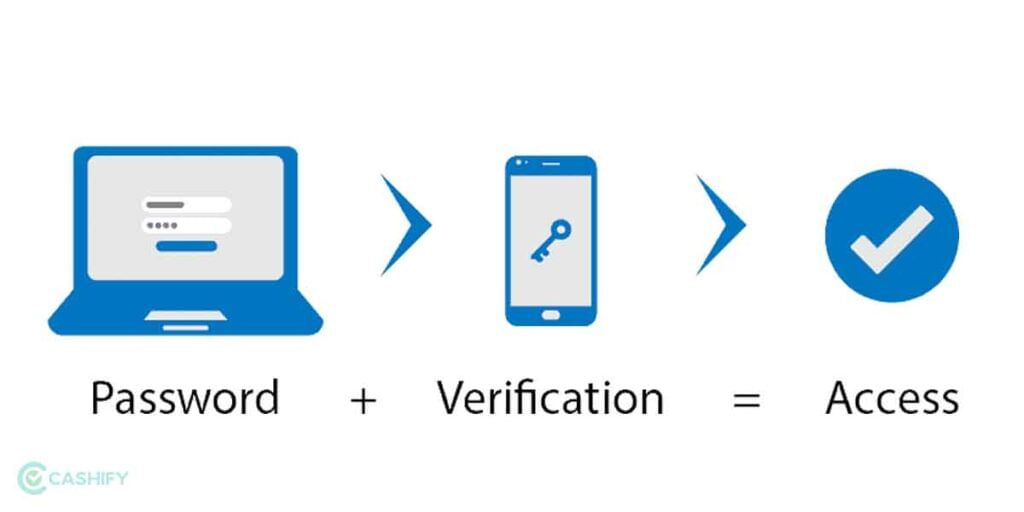
3. Enable Multi-Factor Authentication
How many times would you feel annoyed entering a password on your social media or email or net banking account? Turns out cracking a single password is easy depending on what you have set as your password. However, multifactor or 2-Factor Authentication allows setting up two varied means of the password such as an actual password and an OTP on your phone or via Google Authenticator.
It helps ensure the said account remains safe from any cyberattacks since the accused will have to make more efforts to crack the password. Moreover, you can set fingerprint, FaceID, and other ways for authentication to ensure higher resistance against such attempts.
4. Handle Passwords With Care
A general user would keep simple passwords such as birth dates or strings of name and some number to protect social media, email, bank accounts, etc. The thing with these passwords is, they are easy to get access with modern tools that can decipher thousands of passwords in mere seconds. It becomes critical to handle passwords with extreme responsibility to prevent any breach of security.
Modern solutions include password vaults and Privileged access management (PAM) solutions among others. There are some hard rules to keep in mind such as associating separate passwords with different accounts. Make these strings difficult to guess and of course, change it at the internals. There’s also common sense that one shouldn’t share or write down the password endangering the security of the said account whatsoever.
5. Back-Up
In the event of a ransomware attack, all your data is held captive until you transfer a said amount. Ransomware is on the rise with at least 321 instances reported in 2021 and the numbers are growing up. Apart from that, data loss due to malware or other irritants can put the user in trouble as the data might be of extreme importance.
In any case, it is crucial to keep a backup of the data encrypted from time to time. Apart from that, you must update the system frequently and provide privileged access to restrict unwanted access at random.
6. Conduct Cybersecurity Audits
As it is righteous to say that prevention is better than cure. Turns out that conducting a complete audit of the organizations, websites, and systems in use is critical. This gives a clear picture of any precursor to security flaws or loopholes that attackers might exploit. It helps find invisible holes in the system and curb any vulnerabilities.
Conducting a thorough cybersecurity audit enables removing privileges and access or unused accounts to block their potential aftermath. There’s always a tonne of data including metadata, session records, etc, that systems collect from time to time. These data points may not look like much but can reveal a lot about an organization or an individual. Thus, a thorough audit will help iron out any discrepancies thereby putting a brake on potential future incidents.
Also Read: The Future Of Artificial Intelligence: Applications & Implications